 Page Summary
Page Summary
DoD plans to implement a new Cybersecurity framework called CMMC (Cybersecurity Maturity Model Certification) to assess and enhance the security posture of the Defense Industrial Base (DIB).
Recent events have caused the DoD to look hard at how defense contracts store, share, and deliver sensitive data within their corporate technology infrastructures. Data is being leaked at an unprecedented level and cost American taxpayers millions if not billions of dollars. The DoD is also reporting that these data leaks are allowing its adversaries to increase military capabilities, further closing the technological gap with American defense ingenuity.
AtWork's Cybersecurity Keeps You Secure and Compliant
and governance. Develop, execute, and maintain the cybersecurity to keep you protected and compliant.
To date, there are several different cybersecurity frameworks and standardizing organizations (CSA, ISO, PCI, HIPAA, NIST) that are used across different industries that are specific to each but are all meant to protect sensitive data. For it's , the DoD is leaning on NIST
(National Institute of Standards and Technology) and their long history of producing technology and security standards has a catalog of frameworks, each geared towards a specific use case. NIST has developed SP 800-171, designed to protect sensitive data in unclassified environments.
The CMMC is intended to serve as a verification mechanism to verify appropriate levels of cybersecurity practices and processes are in place. From basic cyber hygiene to protecting controlled unclassified information (CUI) that resides on the Department’s industry partners’ networks. This will enact a third-party audit, to verify the standards within NIST 800-171 are being followed. Once the audit is completed, the organization will be certified at the appropriate CMMC level.
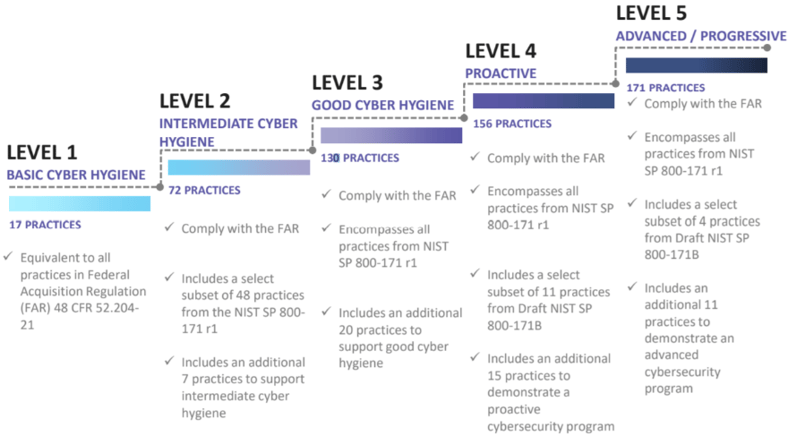
Eventually, the intent is to incorporate CMMC into Defense Federal Acquisition Regulation Supplement (DFARS) and use it as a requirement for contract awards. DFARS section (paragraph 252-204-7012) outlines the current requirements, which include NIST 800-171 self-attestation today, but the DoD knows that this approach might not yield better security standards. It's also important to note the additional sub-paragraphs that fall outside of NIST 800-171 and the potential CMMC (252-204-7012 Paragraphs c-g).
This can seem like a daunting task, even for the most mature organizations and though the standard has not been written into law, the odds are that it will be very soon. It's best to start preparing yourself and your organization to be ahead of the curve. Here are questions you should be asking.
- Where do we start?
- What does our current IT security program look like?
- What steps do we need to take to start the process?
- What should your System Security Plan (SSP) include?
- How can you implement the requirements to enable CMMC validation?
Chances are you will need outside resources to help with the process and potential tools, to help track and provide insight on progress as you embark on this journey.
Additional Resources:
- NIST SP 800-171: https://csrc.nist.gov/publications/detail/sp/800-171/rev-2/final
- DFARS 252.204.7012: https://www.acquisition.gov/dfars/252.204-7012-safeguarding-covered-defense-information-and-cyber-incident-reporting
